Are you tired of juggling countless passwords, struggling to remember which combination unlocks which account? It's time to embrace a world where secure access doesn't equal endless frustration. The future of digital security lies in simplified authentication methods, and businesses that prioritize user experience are leading the charge.
The digital landscape is ever-evolving, and with it, the threats to our online security become more sophisticated. Traditional password-based systems are increasingly vulnerable, leaving individuals and organizations susceptible to breaches, phishing attacks, and credential stuffing. This has fueled the demand for innovative authentication solutions that prioritize both security and user convenience. The keyword here is "simplify authentication," making the process easier and more secure.
| Category | Information |
| Concept | Simplified Authentication & Secure Logins |
| Benefits | Improved user experience, enhanced security posture, streamlined workflows, reduced IT burden, increased user adoption. |
| Methods | Single Sign-On (SSO), Passwordless Authentication (Magic Links, Biometrics, OTPs), Multi-Factor Authentication (MFA). |
| Technologies | SAML, OAuth 2.0, OpenID Connect, FIDO2, Authentication Apps, Hardware Tokens |
| Vendors | Twilio, Signeasy, LastPass (mention for comparative analysis) |
| Vulnerabilities of Password Managers | Phishing Attacks, Keylogging, Data Breaches at Password Manager Company, Weak Master Password |
| IAM System | Robust Identity and Access Management (IAM) system ensures the right people access the right systems at the right time. |
| Reference Website | Okta - What is Authentication? |
Single Sign-On (SSO) is rapidly becoming a standard, allowing users to access multiple applications with a single set of credentials. This not only streamlines the login process but also reduces the risk associated with managing numerous passwords. Signeasy, for example, leverages SSO to provide users with seamless access using their existing corporate credentials, whether it's Google or Microsoft 365 logins. This simplifies the user experience while simultaneously bolstering security.
- Scam Alerts Safe Checks Filmyflyfoo And Beyond
- Vegamovies 4k 60fps Experience Smooth Streaming Find Out More
The implementation of SSO has several tangible benefits. Workflows are streamlined as employees no longer need to waste time repeatedly entering passwords. Access management becomes significantly easier, allowing IT departments to efficiently manage user permissions and deprovision accounts when employees leave the company. Furthermore, SSO enhances the overall security posture by leveraging existing authentication frameworks and reducing the attack surface associated with multiple passwords.
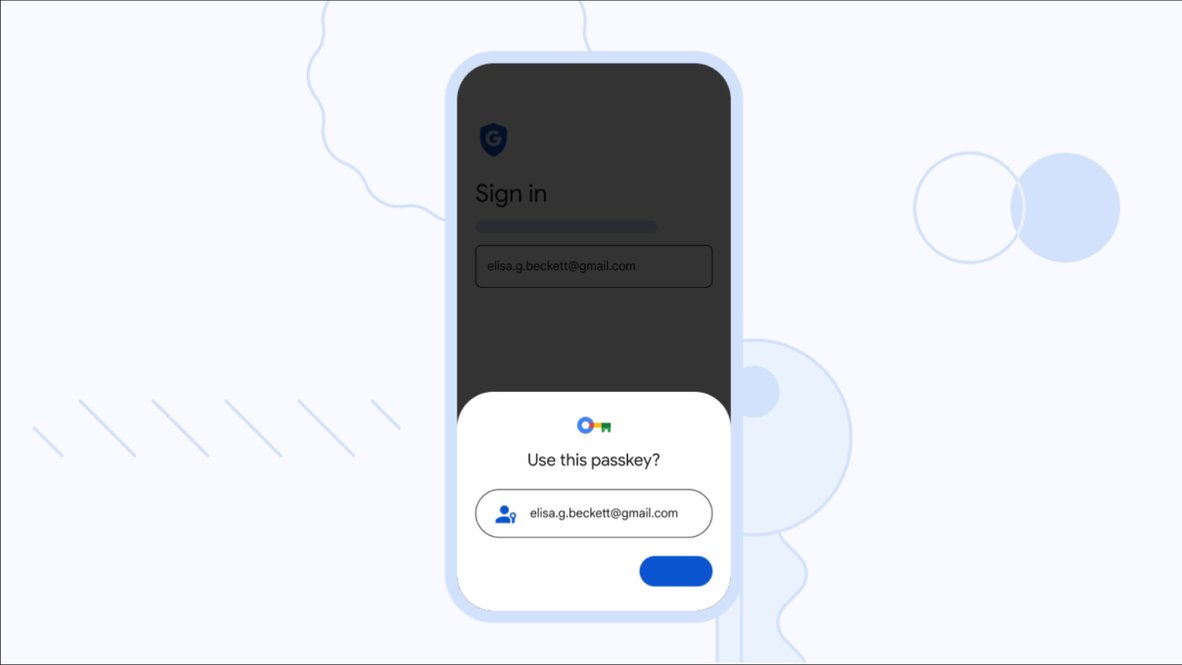
Passwordless authentication is another promising approach. By eliminating static passwords altogether, businesses can mitigate the risks associated with phishing, credential stuffing, and password reuse. Methods like magic links, SMS one-time passwords (OTPs), and biometric authentication offer secure and convenient alternatives. Imagine a scenario where users can simply click a link in their email inbox to gain access to an application no password required. This "magic link" approach not only simplifies the login process but also significantly reduces the risk of unauthorized access.
Of course, no security solution is foolproof. Even robust password managers like LastPass are vulnerable to certain threats. Phishing attacks, for instance, can trick users into revealing their master passwords, granting attackers access to all their stored credentials. Therefore, it's crucial to implement a multi-layered security approach that combines strong authentication methods with user education and awareness training.
- Bolly4u More Finding Bollywood Movies Online In 2024
- Lee Min Ho Married Fact Vs Rumors His Relationship Status 2024
Twilio offers user authentication and identity solutions designed to help businesses secure user logins and manage user identities effectively. These solutions often incorporate features like multi-factor authentication (MFA) and adaptive authentication, which dynamically adjust security measures based on user behavior and risk factors.
When implementing secure login systems, it's essential to choose the right authentication protocols and technologies. SAML (Security Assertion Markup Language), OAuth 2.0, OpenID Connect, and FIDO2 are all widely used standards that offer varying levels of security and flexibility. The choice of protocol will depend on the specific needs of the application and the organization's security requirements.
In addition to strong authentication methods, it's also crucial to implement robust access control policies. This involves limiting user permissions to only what's necessary for their job functions. A robust Identity and Access Management (IAM) system ensures that the right people have access to the right systems at the right time, minimizing the risk of insider threats and data breaches.
The importance of secure logins in web applications cannot be overstated. Authentication is the cornerstone of any secure application, ensuring that only authorized users can access sensitive data and features. By improving the login experience, websites can increase user engagement and trust, while simultaneously reducing the risk of security breaches.
However, managing multiple logins can be a burden for both users and IT teams. Users struggle to remember numerous passwords, leading to password fatigue and risky behavior like password reuse. IT teams, on the other hand, face the challenge of managing user accounts, resetting passwords, and responding to security incidents.
Ultimately, simplifying access with passwordless SSO offers a win-win solution for both users and organizations. By streamlining the login process and enhancing security, businesses can create a more user-friendly and secure online experience. As the digital landscape continues to evolve, simplified authentication will become increasingly critical for maintaining a strong security posture and fostering user trust.
Imagine the peace of mind knowing that your team members' access is instantly revoked the moment they leave the company. This is the power of a well-integrated and centrally managed authentication system. No more lingering accounts or forgotten passwords posing a security risk.
The shift towards simpler logins isn't just about convenience; it's about fundamentally changing user behavior. By making secure authentication effortless, users are more likely to adopt it, effectively moving away from risky password habits and embracing a more secure way of accessing their digital lives.


Detail Author:
- Name : Bella Howe
- Username : bret.abshire
- Email : medhurst.dasia@gmail.com
- Birthdate : 1988-01-30
- Address : 4849 D'Amore Rapid Lake Luisa, MD 67190
- Phone : +1.865.516.0453
- Company : Armstrong-Bins
- Job : Internist
- Bio : Nihil dolorum cumque voluptatem. Incidunt minima hic nobis. Qui quod quas inventore est est iusto eum. Magni accusamus dolorem deserunt alias.
Socials
tiktok:
- url : https://tiktok.com/@isadorefritsch
- username : isadorefritsch
- bio : Nemo similique aut tempore animi qui praesentium qui.
- followers : 6594
- following : 913
twitter:
- url : https://twitter.com/fritschi
- username : fritschi
- bio : Et eius harum veniam. Quidem enim ipsum officia modi quos. Explicabo rerum ducimus officia provident.
- followers : 2883
- following : 2863
linkedin:
- url : https://linkedin.com/in/ifritsch
- username : ifritsch
- bio : Quas ad nemo repudiandae eveniet est magnam id.
- followers : 5398
- following : 1094
facebook:
- url : https://facebook.com/isadore.fritsch
- username : isadore.fritsch
- bio : Distinctio est ex labore quis laudantium repellendus.
- followers : 6751
- following : 1829
instagram:
- url : https://instagram.com/isadore_xx
- username : isadore_xx
- bio : Velit consectetur tenetur animi. Architecto ut accusamus dolorem expedita et.
- followers : 5314
- following : 283